tfplan2md Solves This
-
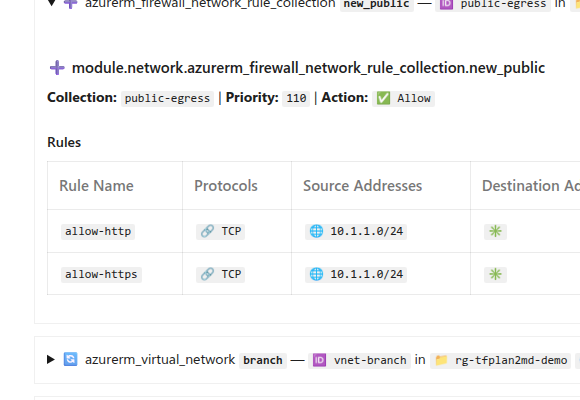
Security Changes as Readable Tables
Firewall and NSG rules rendered with protocols, ports, and actions
-
Friendly Names, Not GUIDs
Principal IDs, role names, and scopes resolved to readable text
-
Inline Diffs for Large Values
Shows computed diffs for large values like JSON policies or scripts
-
Optimized for PR Comments
Designed and tested for GitHub and Azure DevOps rendering
Click to enlarge